BLUFF
- Non-State Actors (NSAs) are relying on open-source platforms to adopt and iterate on drones across geographies, compressing innovation cycles and accelerating downstream mutations.
- Fluid knowledge networks are spiking NSA’s risk appetites by bridging the gap between what exists and what can be possible on the battlefield. With adversarial groups perceiving drones as a major power equalizer, security and operational risks are expected to exacerbate across various realms.
- Hostile drone data transfers are outpacing those of traditional actors by preserving instrumentality and agility over ideals and safety. This has rendered the siloed approach to troubleshooting problems and developing expensive solutions obsolete.
NSAs are leapfrogging drone development by changing the way they collect and learn information. Through decentralized digital networks, peer-to-peer learning, and battlefield-to-workshops feedback loops, these groups now iterate drone capabilities almost 3-5x faster than state defence programs. The current digital landscape provides NSAs with democratized access to drone intelligence previously confined to classified networks. Telegram channels, Discord servers, Reddit communities, YouTube tactical analysis channels, and darknet forums function as open-source data points, operating beneath state monitoring thresholds.
These open-source hubs are fostering intellectual spaces where ideas are incubated, new inspirations are shared, and course correction is freely distributed. As a result, NSAs no longer await transfers from their state patrons to undertake change, they have begun to adapt & innovate faster than ever on their own. By leveraging online information channels that transcend geographical boundaries, NSAs are discovering unique use cases for drones that are cheap and agile.

This shift in the learning process has a two-fold impact on NSA's drone capabilities: First, NSA’s risk appetites have spiked massively across conflict theaters. Actors are flooded with new inspirations for drone use cases on the internet, which portray drones as the ultimate asymmetric weapon to upend the power imbalance in a conflict. This perspective has spurred NSAs to actively induct weaponized drones in their arsenals and undertake riskier operations to assert control. In the process, new frontiers, thresholds, and red lines are being established across the world.
Second, digital distribution of technical & tactical knowledge has compressed iteration cycles and bridged performance gaps that used to take months or even years. While the easy availability of resources to learn itself does not translate into an effective execution of these tactics, it has significantly lowered the learning threshold and provided the first step for the NSAs to mirror the wins of others. Procedural hurdles in this journey can be troubleshot across several encrypted online groups that have simplified problem-solving for new entrants. With knowledge fluid and help affordable, transposing drone use cases from one region to another becomes imminent.
Tactical problems are now solved async, individuals post challenges to forums at night and wake to crowdsourced solutions from global contributors spanning time zones. This 24/7 distributed problem-solving system compresses months of trial and error into days by directing resources toward collaborative iteration with anonymous experts, hobbyists and enthusiasts, who often remain unaware of exactly how their advice will be used. By embedding themselves in a complex web of online and offline intelligence channels, NSAs are hedging their bets on future drone progress
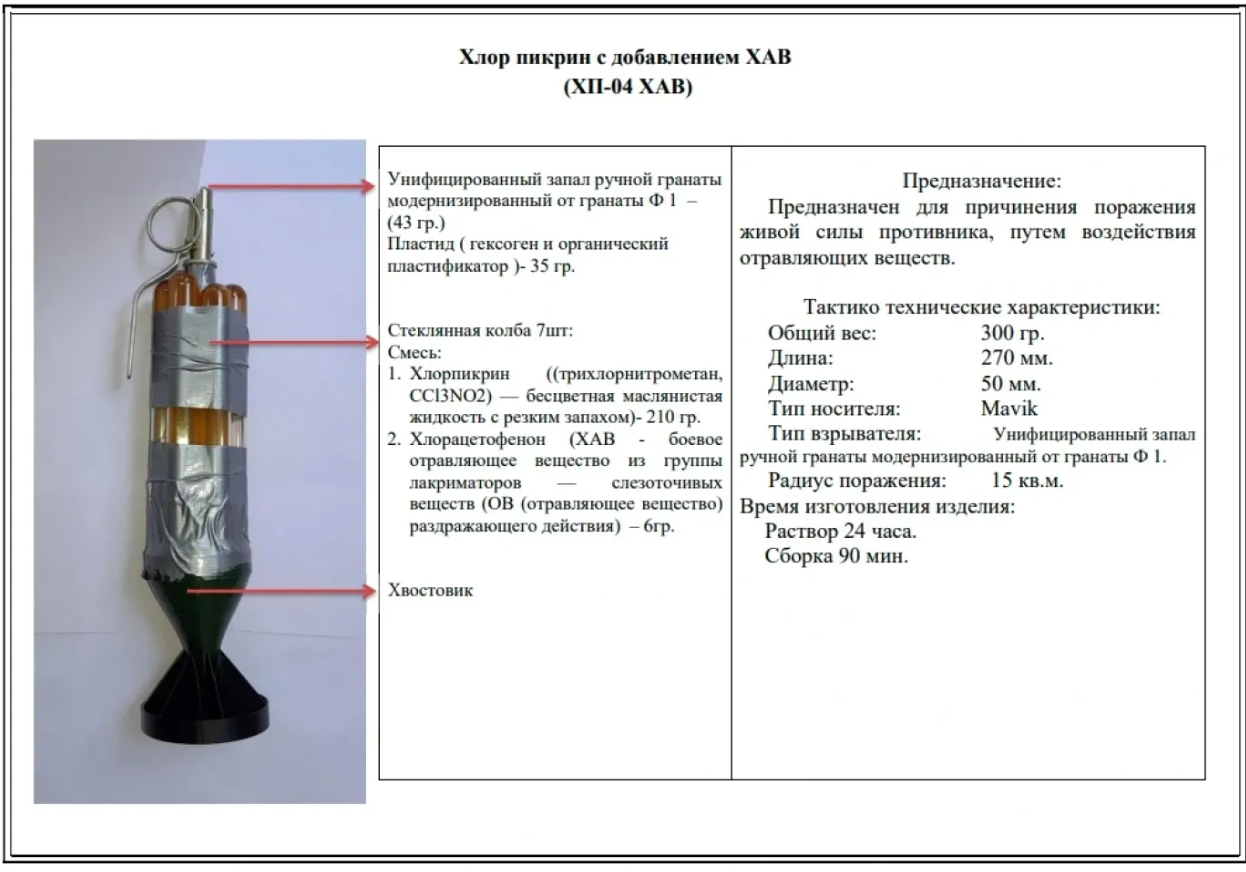
These channels can be parallel, layered and sometimes overlapping, wherein drone data is shared extensively in multimodal formats, including videos and instructional manuals. Actors with larger resource pools have taken it a step further by integrating human intelligence sources, i.e., veteran drone operators, to directly tailor and inject field knowledge from conflict zones into their specific operations. For example, the Cartels in Latin America contracted Ukrainian drone operators to impart their tactical expertise of cutting-edge drone technology, thereby potentially springboarding localized innovations. Although smaller NSAs rely heavily on online sources due to budget constraints, they leverage drone content posted by bigger groups for intelligence gathering.
It is not only the states vying to attract the top drone talent. A rising demand for Ukrainian and Russian drone operators is likely underway in the NSA community.
Tactics, Techniques, and Procedures (TTPs) now propagate through network effects rather than hierarchical chains. Traditional intelligence models assumed linear transfers: State → Proxy → Battlefield. Often, NSAs with state sponsors largely employed drones with identical structural and operational capabilities as their patrons. Later, drones were produced indigenously by proxies to optimize efficiency, expedite supply, and meet contextual needs. However, this developmental cycle has experienced a major shift with the advent of Commercial-Off-The-Shelf (COTS) and information availability online. The current state reflects a multi-directional reality spurred by growing digital diffusion and minimal direct contact. These emerging transfer pathways require better methods of tracing technology transfers and innovation flows.

NSAs are carefully observing those who are rapidly adopting, developing, and improving COTS to learn with minimal risks and costs. Learning from the supply bottlenecks in Ukraine, several NSAs have realized that the fastest way to ship and innovate low-cost drones is to establish streamlined feedback loops and ramp up in-house production units. Instead of reinventing the wheel, they have embraced a proven method to their advantage. With NSAs sourcing information from digital spaces, actors in Africa can learn from drone operators in Asia, who can learn from operators in Latin America and vice versa.
In today’s threat landscape, focusing primarily on relational tracing for predicting innovation flows will result in suboptimal counterstrategies. Instead, a more robust methodology is imperative that rapidly integrates data across digital spaces with strategic knowledge to forecast TTP transfers proactively. While this comes with its own set of challenges involving information validation, monitoring digital spaces will future-proof counterstrategies as more actors shift online for information gathering.
Building a dynamic catalogue on adversarial drone innovations, including tactical sequencing, specific use cases, and emerging innovations worldwide across NSAs, will strengthen threat assessment, scenario development, and drone threat forecasting. A proactive tracking of intelligence and innovation flows across NSAs, leveraging emerging technologies to comb through digital spaces, must be a strategic priority to outmaneuver highly resilient and adaptive actors. Unlike conventional reactive methods reliant on siloed information gathering, an iterative model for predicting drone transfers prioritizes real-time alignment with adversarial threats, if not a proactive edge.



